It’s a normal day, John strolls into his clinic clutching a steaming cup of coffee, as the beams of sunlight reflect from the tall glass windows that surround the reception area. Everything is as usual, a typical day in the life of a healthcare worker. John enters the front door and, as the morning reflections fade, his eyes refocus to behold terror on the faces of the receptionists and nurses scrambling about.
“There’s been a breach, John. It was caused by YOU!”
Despite the passing of HIPAA Law in 1996 and subsequent updates to protect patient’s privacy and security we are seeing more infringements than ever. Living in 2019 we have seen some truly dumbfounding scandals from hospitals, insurers and small local clinics alike.
The days of only the big financial institutions being targeted are long gone; anyone and everyone who holds patient records is a target.
Nowadays, it’s not the disgruntled high school students compromising systems for fun, boredom or, as in “Ferris Buller’s Day Off,” to change attendance records. Modern attacks are performed by sophisticated networks of cyber criminals using complex hacking tools.
Despite the plethora of attack vectors, below are 3 common faults that enable attackers and lead to patient’s data being lost or stolen.
1. Lack of two-factor authentication for health systems
Going back to our example of John, the night before the breach he had received a seemingly innocent email. It came from ADP which his company uses to process payroll.
The email informed him that he needed to update his account info immediately or have delays in receiving his paycheck. John clicked through the email’s links without questioning the authenticity and entered his system credentials into a website with a strange URL. It redirected him out of the page after capturing his credentials and after a long day John decided to return home and talk to HR later.
What John didn’t know is that a malicious user had created the fake email and fake login page to capture John’s credentials. Those stolen credentials were then used to connect to and compromise the clinics networks and systems overnight from a remote location.
The systems had no secondary means of verifying the user’s identity and thus allowed full access. This can be prevented by implementing multi-factor authentication, which uses a text message, phone permissions or email to validate logins, on top of the username and password.
2. Failure to keep systems up to date with patches
After the hacker infiltrated the clinics healthcare systems using John’s credentials, they still had a problem. John wasn’t the primary admin and did not have access to each of the clinic’s patient records.
The savvy hacker looked up the name of the system in a web search and found the common vulnerabilities listed online. Vendors publish known vulnerabilities along with patches that fix these issues so users can protect their systems.
Unfortunately, John’s clinic outsourced their IT but seldom communicated with their IT firm — usually only when there was a problem. The hacker noticed that their IT managers had not run a few of the patches from the vendor’s website and exploited these known vulnerabilities to get full admin privilege.
3. Storing sensitive data in plaintext form
Now that the hacker has full access to the system’s collection of patient records, they typically have another issue – all the records are kept in an encrypted and unreadable form.
Encryption, which HIPAA Law requires for sensitive PHI or protected health information, renders records useless to hackers. However, once again the IT team did not properly encrypt all of the system and the malicious actor stole hundreds of confidential records.
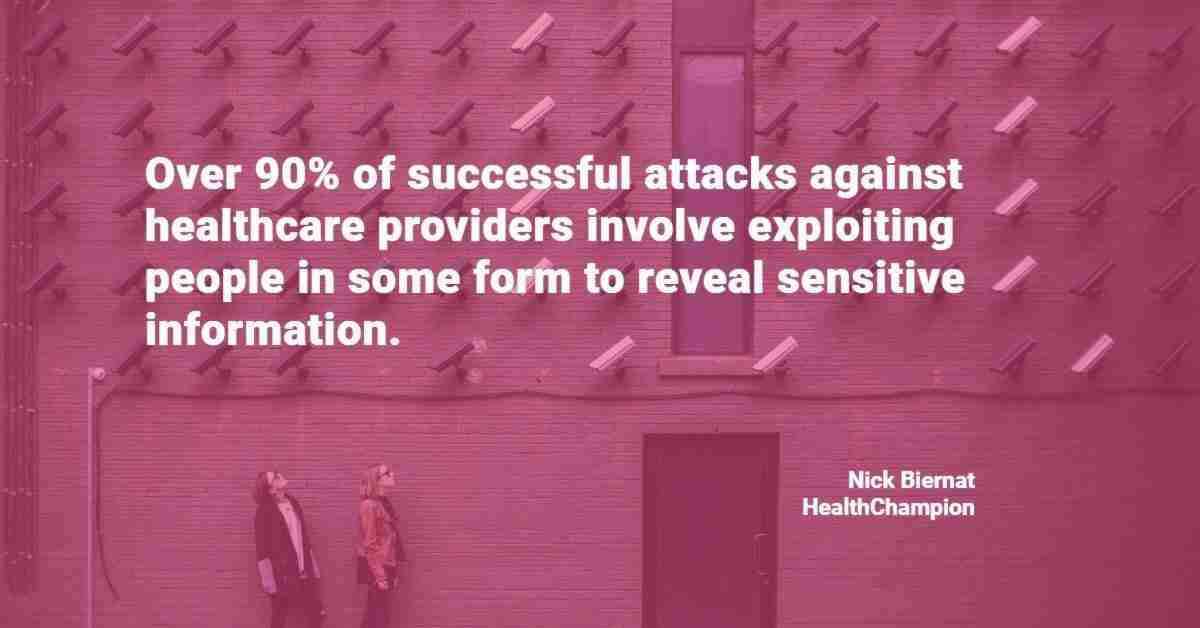
A lack of awareness and training is the biggest contributor to the poor state of cybersecurity. Well over 90% of successful attacks against healthcare providers involve exploiting people in some form to reveal sensitive information, and therefore the most effective way of preventing an attack is to invest in a comprehensive and periodic training program for staff.
Stakeholders can also boost their organizations’ cybersecurity efforts by enabling multi-factor authentication for all user accounts. It is by far the fastest, least costly and most simple way to drastically reduce a criminal’s chances of exploiting healthcare systems.